Hello! I'm Furuya from Quality Control.
Since we learned about symmetric key cryptography and public key cryptography, let's start with thesymmetric key cryptosystemI would like to introduce the
Click here for table of contents
- 1. why is the encryption of the Internet communication necessary?
- 2. "Plaintext", "Encryption", "Decryption", and "Key".
- 3. what is "symmetric key cryptosystem"?
Why is the encryption of Internet communication necessary?
Why is it necessary to encrypt Internet communications in the first place?
I think everyone is using all kinds of internet services by using PC or smart phone everyday. Online shopping, online banking, Youtube, games, emails and so on.
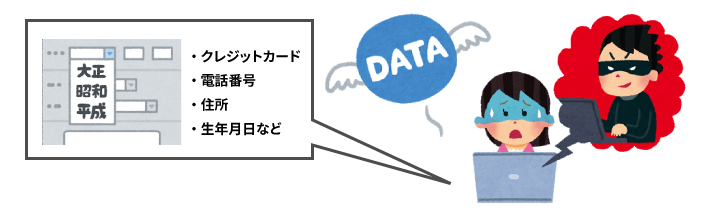
For example, when you shop online, you need to provide your credit card, address, phone number, etc.personal informationYou have entered the following information to make a purchase. If this kind of information is stolen by a malicious third party without permission, it would be very bad.
And that's where you come in.Technology of the encryption of the Internet communicationwill be.
[What is the encryption of Internet communications?
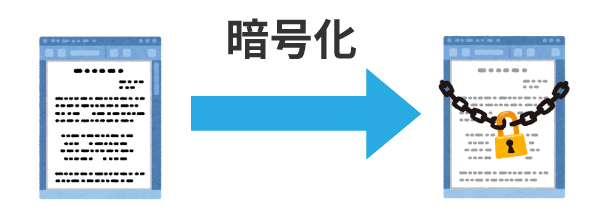
Make sure that even if a malicious third party steals the information without permission, they will not be able to understand what is written.
About "Plaintext", "Encryption", "Decryption", and "Key
In introducing the symmetric key cryptosystem, there is a word that must be explained first.
"plaintext," "encrypt," "decrypt," "key.About.
What's a "plaintext"?
Unencrypted data is called "plain text".It is called
Plaintext refers to data that makes sense without any special processing or decoding.
In the past, it was called "plaintext" because it was mainly used to encrypt text, but now it is considered "plaintext" to include not only text but also data such as images and audio.
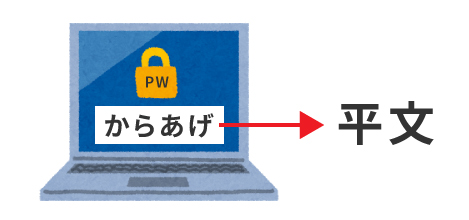
For example, when I tried to do shopping on the Internet, I entered the following password to register as a member. (*Normally, it is alphanumeric, but for the sake of clarity, I will use Japanese in the example)
PW:.fried (e.g. potatoes, chicken)
This password, "Karaage,""Plain text.Per the
What is "encryption"?
Based on certain rules.The conversion of "plaintext" into "ciphertext" is called "encryption.It is called
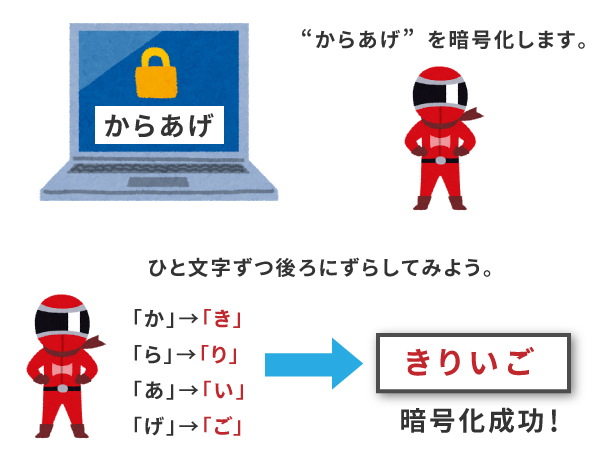
Let's try to encrypt the password "karaage" using the rule in the previous example.
RULES.Move back one letter at a time.
"Or..."Kiki.
"et al.Li.
Ah.No, no, no.
"Get."Word.
The password is encrypted and "Kiriigo." now. This way, even if a third party sees it, they won't know what it means.
What is "decryption"?
The return of ciphertext to plaintext is called decryption.It is called
Let's take the previous example, the encrypted sentence "kiriigo", and "decrypt" it using the rules.
RULES. "The rule was to move back one letter at a time, so we're going to do the opposite, move back one letter at a time.
"Ki."or...
"Riri."La.
Yes.Oh.
"Go."Hair.
This will change the password to the original "Karaage." I returned to the
In this way, we can restore the original shape of the"Decryption.I say.

What's a "key"?
As explained in the example, "shift one letter at a time".The data used to perform encryption and compounding is called the "key".It is called

What is "symmetric key cryptography"?
Common Key Cryptography.indicates word or phrase being definedA cryptographic method in which the sender (the encryptor) and the receiver (the decryptor) use the same key (symmetric key).This refers to the
This key must be kept secret because it is useless if it is known to a third party. For this reason, the "symmetric key" is also called the "secret key", and the "symmetric key cryptosystem" is also called the "secret key cryptosystem".
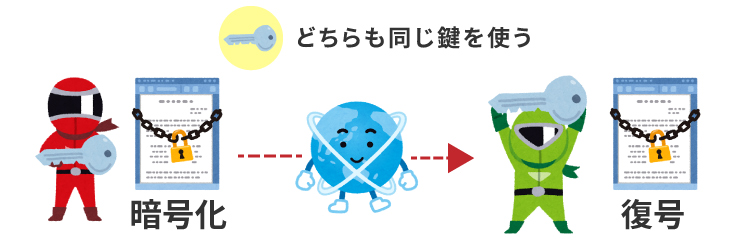
Now let's review with an example.
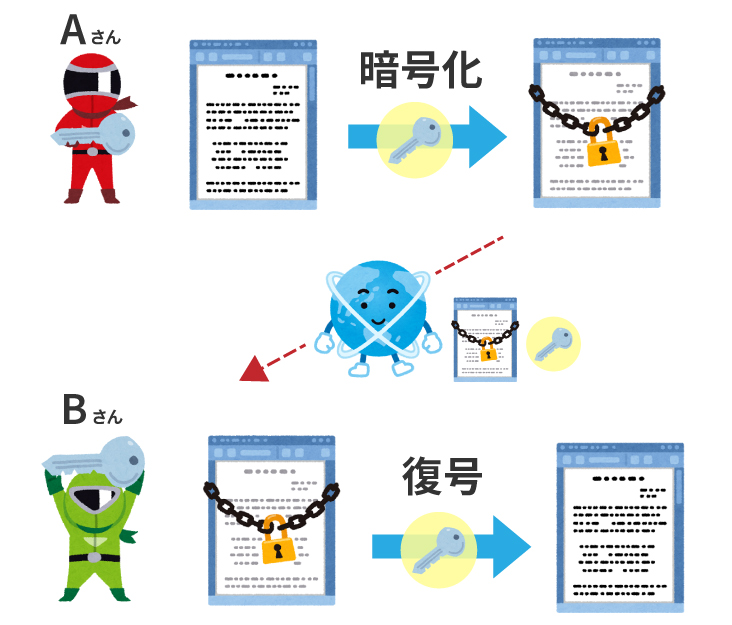
For example, let's say "Mr. A" sends data to "Mr. B".
1. Mr. A encrypts data using a "common key".
Mr. A sends the "encrypted data" and the "common key" to Mr. B.
Mr. B received the "encrypted data" and the "common key" from Mr. A.
Mr. B decrypts (restores) the "encrypted data" using the "common key" he received.
This method of "encryption" and "decryption" using the same key is called "symmetric key cryptosystem".
The advantage is that you can decrypt it as long as you have the key.
One of the disadvantages is that the keys must be stored and handed over securely, as it is useless if the keys fall into the hands of a malicious third party. And as the number of people exchanging data increases, the number of keys that need to be managed swells.
And that's where you come in."Public Key Cryptography..
About this, I want to explain again! This time, as the first story of the encryption, I explained about "Common Key Cryptosystem", together with "encryption", "decryption" and "key".
We look forward to working with you again next time.
・Mechanism and characteristics of symmetric key cryptography and public key cryptography
・Public Key Cryptosystem and Symmetric Key Cryptosystem - PKI Basics 1
Kitami Style Illustration IT School IT Passport

